You lock your doors, set up home alarms, and keep valuables in safes—but how do you protect your digital life? Every day, billions of people send messages, access bank accounts, store personal data in the cloud, and work remotely using connected devices. Behind all of this activity lies an invisible battleground—cybersecurity.
Cybersecurity isn’t just a concern for tech companies or IT professionals. It’s a vital layer of protection that touches everything: your identity, your money, your privacy—even your safety. From the moment you connect to the internet, you’re exposed to threats ranging from phishing emails to ransomware attacks. And with more devices going online each day, the risks are growing.
Yet despite the increasing complexity of attacks, most people still don’t fully understand what cybersecurity really is or how it works. This guide will walk you through the essential concepts, technologies, and real-world practices that form the foundation of cybersecurity—from protecting personal data to securing enterprise infrastructure.
If you’ve ever asked yourself, “Am I really safe online?”, then this article is for you.
Understanding Cybersecurity in a Digital-First World
What Is Cybersecurity and Why It Matters
At its core, cybersecurity refers to the practice of defending computers, servers, mobile devices, networks, and data from malicious attacks. It encompasses everything from protecting personal email accounts to securing enterprise-level databases from breaches. Cybersecurity is not a single tool or software—it’s a strategic approach to digital safety.
In a world where data is currency and connectivity drives productivity, the stakes have never been higher. A successful cyberattack can shut down hospitals, drain bank accounts, leak sensitive documents, or compromise personal identities. For businesses, it can result in massive financial losses, legal liabilities, and irreversible damage to reputation.
The Evolution of Cybersecurity Threats
Cyber threats have grown exponentially in both volume and sophistication. In the early days, viruses spread through floppy disks or suspicious email attachments. Today, attackers use advanced techniques like zero-day exploits, AI-generated phishing emails, and multi-vector ransomware that can infiltrate global networks within minutes.
Consider these milestones in cybercrime evolution:
- 1990s: Email viruses like Melissa and ILOVEYOU caused widespread disruptions.
- 2000s: Worms and trojans began exploiting browser vulnerabilities.
- 2010s: Rise of ransomware (e.g., WannaCry) and state-sponsored attacks.
- 2020s: Supply chain attacks (e.g., SolarWinds), deepfakes, and AI-driven threats dominate headlines.
Modern cyberattacks are no longer random—they are targeted, persistent, and profit-driven. They may be launched by lone hackers, organized crime groups, or even nation-states. And with the rise of cloud computing, Internet of Things (IoT), and remote work, the attack surface is larger than ever.
Cybersecurity Is Everyone’s Responsibility
One of the biggest misconceptions is that cybersecurity is solely the job of IT departments. In reality, every internet user plays a role. Clicking on a phishing link, using weak passwords, or ignoring system updates can open the door to a breach.
From individual users to enterprise leaders, the mindset must shift: Cybersecurity is no longer optional—it’s essential.
It requires awareness, action, and accountability at every level.
Whether you’re a student, a freelancer, a small business owner, or a global enterprise—understanding the basics of cybersecurity is the first step toward staying protected.
The Core Pillars of Cybersecurity
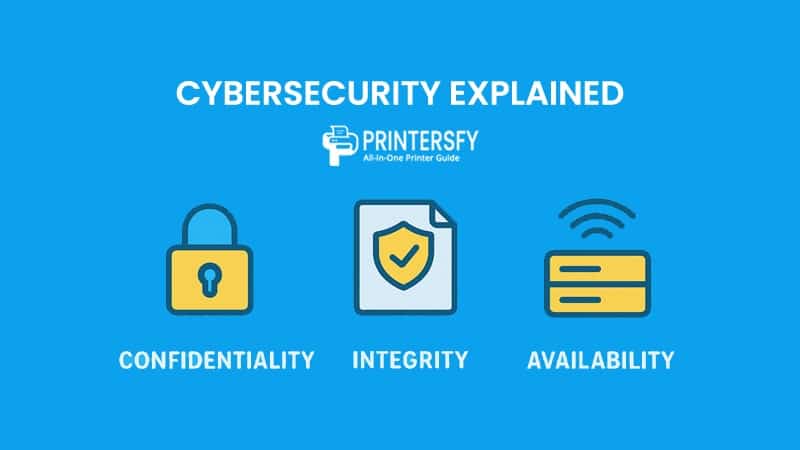
Confidentiality
Confidentiality in cybersecurity ensures that sensitive information is accessible only to those who are authorized to see it. This is the most intuitive pillar—when we think about security, we often think about keeping secrets safe.
Practical examples include:
- Encryption of messages and files to prevent unauthorized access
- User authentication (like passwords and biometric scans) to verify identity
- Access controls to limit who can view or modify specific data
When confidentiality is breached, the consequences can be serious—from personal identity theft to exposure of trade secrets or classified government information.
Integrity
Integrity refers to maintaining the accuracy and trustworthiness of data. It ensures that information is not altered, tampered with, or deleted—either intentionally or unintentionally—during storage or transmission.
Real-world examples:
- Checksums or digital signatures to verify that a file hasn’t been modified
- Version control systems in software development
- Audit logs to track changes and identify tampering
Integrity is especially important in sectors like finance, healthcare, and legal services where even the slightest data modification can have legal or life-threatening implications.
Availability
Availability ensures that data and services are accessible when needed. No matter how secure a system is, if legitimate users can’t access it at critical moments, it fails its purpose.
Common threats to availability include:
- DDoS (Distributed Denial of Service) attacks that flood servers
- Hardware failures or power outages without failover systems
- Ransomware attacks that encrypt files and lock out users
To ensure availability, organizations use redundant systems, backups, disaster recovery plans, and cloud infrastructure that can scale and recover quickly.
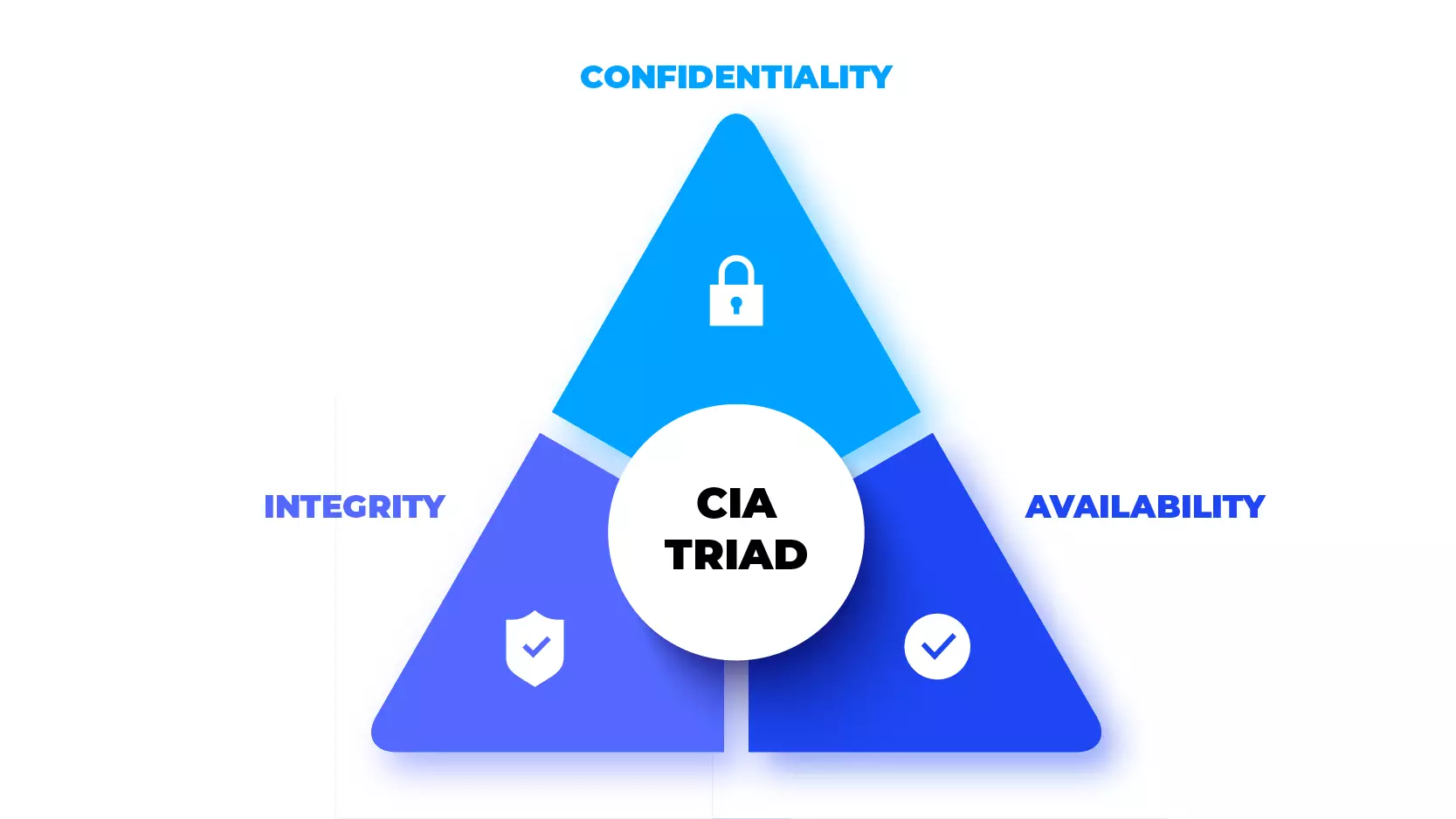
Understanding the CIA Triad
These three principles—Confidentiality, Integrity, and Availability—form the CIA Triad, a foundational model used in cybersecurity. Every security decision, from designing a password policy to choosing a cloud provider, should aim to balance these three pillars.
📌 Example Scenario:
Imagine a hospital’s electronic health records system:
- Confidentiality keeps patient data private.
- Integrity ensures the medical records are accurate.
- Availability guarantees doctors can access the data instantly during emergencies.
Compromising any part of this triad can lead to operational, ethical, or legal disasters.
Common Types of Cyber Threats and Attacks

In the constantly evolving digital landscape, cyber threats come in many forms—each with unique characteristics, targets, and methods of attack. Understanding the most common types is essential for both individuals and organizations seeking to build a robust cybersecurity posture.
Malware (Malicious Software)
Malware refers to any software intentionally designed to cause damage or gain unauthorized access. It includes:
- Viruses: Attach to files and replicate when opened.
- Worms: Spread independently through networks.
- Trojans: Disguise as legitimate software but carry malicious payloads.
- Spyware: Secretly monitors user activity.
- Ransomware: Encrypts data and demands payment for access.
Malware is often delivered through infected email attachments, malicious downloads, or compromised websites.
Phishing
Phishing is a social engineering attack that tricks individuals into revealing sensitive information, such as passwords or credit card numbers, by masquerading as a trustworthy entity—often via email or fake websites.
Advanced versions include:
- Spear phishing: Highly targeted and personalized.
- Whaling: Directed at senior executives.
- Smishing: Delivered via SMS.
- Vishing: Delivered via voice call.
Even tech-savvy users can fall victim if the message appears urgent or credible enough.
Man-in-the-Middle (MitM) Attacks
In a MitM attack, a hacker intercepts communication between two parties without their knowledge—typically to steal credentials, spy on data, or alter communication.
Example:
A user connects to public Wi-Fi, and an attacker intercepts login information sent over an unsecured connection.
Countermeasures include:
- Using HTTPS protocols
- Avoiding public Wi-Fi without a VPN
- Implementing network-level encryption
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS)
DoS and DDoS attacks aim to flood a system, server, or network with traffic, rendering it inaccessible to legitimate users. While a single system may launch a DoS attack, DDoS uses multiple compromised devices—often part of a botnet.
Consequences:
- Website downtime
- Lost revenue
- Reputation damage
- Service disruptions in critical infrastructure (e.g., hospitals, airports)
Mitigation tools include traffic filtering, firewalls, and cloud-based DDoS protection services.
Zero-Day Exploits
A zero-day attack targets a software vulnerability that the vendor is unaware of—meaning there’s no patch or fix yet available.
These attacks are especially dangerous because:
- They’re difficult to detect
- They exploit trust in widely used software
- They’re often used in state-sponsored cyberwarfare or espionage
Organizations use intrusion detection systems (IDS) and threat intelligence to spot suspicious behavior before zero-day exploits succeed.
Insider Threats
Insider threats originate from within an organization—often from employees, contractors, or partners who either intentionally or unintentionally compromise systems.
Types include:
- Malicious insiders: Steal data for personal gain.
- Negligent insiders: Cause harm due to carelessness (e.g., using weak passwords).
- Compromised insiders: Infected by malware or social engineering.
Defenses involve user behavior analytics, strict access control, and regular training.
Comparison Table: Common Cyber Threats
| Type of Threat | Attack Method | Primary Target | Impact | Countermeasure |
|---|---|---|---|---|
| Malware | Infected software/files | Individuals, businesses | Data loss, system control | Antivirus, firewalls, patching |
| Phishing | Deceptive emails/sites | Individuals | Credential theft, financial loss | Awareness training, spam filters |
| MitM | Interception of communication | Users on public networks | Data interception, altered transactions | HTTPS, VPNs, encryption |
| DDoS | Traffic overload | Websites, servers | Downtime, service disruption | Load balancing, DDoS protection services |
| Zero-Day | Unknown software vulnerabilities | Software, systems | Remote control, data theft | Threat intel, behavioral monitoring |
| Insider Threat | Internal user behavior | Organizations | Data leaks, operational sabotage | Access control, monitoring, training |
Key Cybersecurity Technologies and Tools
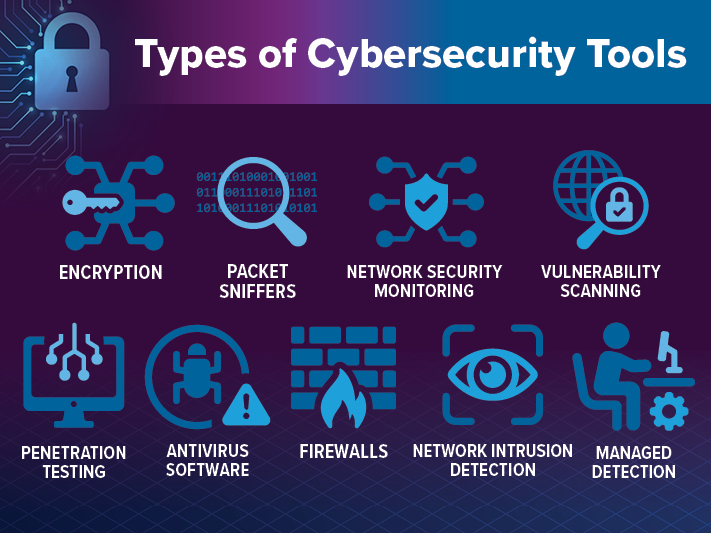
Protecting against cyber threats requires more than awareness—it demands the right cybersecurity technologies tools. Organizations and individuals rely on a broad set of technologies that work together to detect, prevent, and respond to malicious activity. Below are the most essential cybersecurity tools in use today.
Firewalls
Firewalls act as the first line of defense in network security. They monitor incoming and outgoing traffic and enforce predefined rules to block unauthorized access.
There are two main types:
- Network firewalls: Installed at the boundary between a private network and the internet.
- Host-based firewalls: Installed on individual devices to protect them from threats within a local network.
Use cases:
- Blocking suspicious IP addresses
- Preventing port scanning
- Restricting outbound connections from infected devices
Antivirus and Anti-malware Software
These tools detect, isolate, and remove malicious software from devices. While often used interchangeably, antivirus typically targets viruses, while anti-malware addresses a broader range of threats, including spyware, ransomware, and trojans.
Modern solutions use:
- Heuristic analysis to detect new or modified malware
- Cloud-based threat intelligence for real-time protection
- Automatic updates to stay ahead of evolving threats
Example software: Windows Defender, Bitdefender, Malwarebytes, Kaspersky
Encryption
Encryption transforms readable data into unreadable code, making it accessible only to those with the correct decryption key. It’s fundamental to ensuring confidentiality and data integrity—especially during transmission.
Two major types:
- Symmetric encryption: Uses the same key to encrypt and decrypt.
- Asymmetric encryption: Uses a public key to encrypt and a private key to decrypt (e.g., RSA).
Encryption is used in:
- Secure websites (HTTPS)
- Encrypted messaging apps (e.g., Signal, WhatsApp)
- Email services (e.g., PGP encryption)
- Data-at-rest on hard drives or cloud storage
Multi-Factor Authentication (MFA)
MFA requires users to provide two or more verification factors to access an account, significantly reducing the chances of unauthorized access.
Common types of MFA:
- Something you know: Password or PIN
- Something you have: Smartphone or security token
- Something you are: Biometric data like fingerprint or facial recognition
Platforms like Google, Microsoft, and financial institutions now enforce MFA as standard practice.
SIEM (Security Information and Event Management)
SIEM systems collect, analyze, and correlate data from various sources (servers, firewalls, endpoints) to provide real-time alerts and security insights.
Features include:
- Centralized log management
- Anomaly detection
- Automated responses
- Regulatory compliance tracking
Popular SIEM tools: Splunk, IBM QRadar, LogRhythm, Elastic SIEM
SIEM is critical for enterprise-scale environments, enabling security teams to monitor large volumes of data and respond to incidents swiftly.
Additional Tools Often Used in Tandem:
- IDS/IPS (Intrusion Detection/Prevention Systems)
- EDR (Endpoint Detection and Response)
- VPNs (Virtual Private Networks)
- DLP (Data Loss Prevention)
Each of these tools adds a layer of defense to build a defense-in-depth security strategy.
Cybersecurity Best Practices for Individuals and Businesses
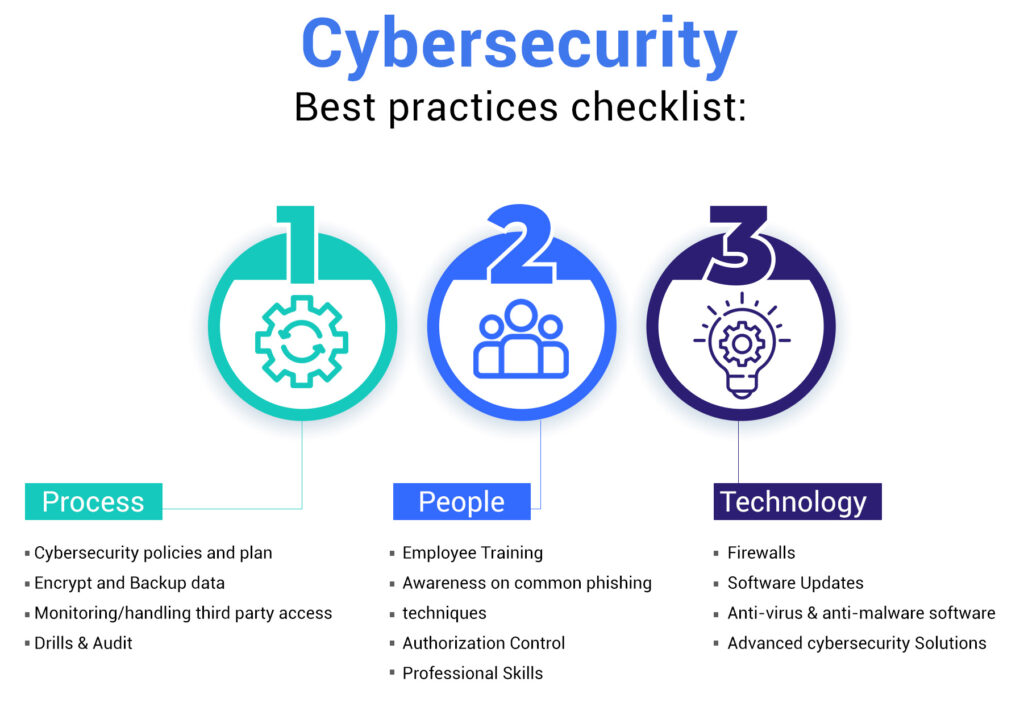
Even the most advanced technologies can’t guarantee full protection without consistent and informed human behavior. Cybersecurity is a shared responsibility, and best practices differ slightly depending on whether you’re an individual user or an organization managing sensitive data at scale.
Best Practices for Individuals
Every connected individual is a potential target for cyber threats. Practicing good cyber hygiene dramatically reduces personal risk.
1. Use Strong, Unique Passwords
- Combine uppercase, lowercase, numbers, and symbols
- Avoid dictionary words or personal info (like birthdays)
- Use a password manager to generate and store complex passwords securely
2. Enable Multi-Factor Authentication (MFA)
- Always activate MFA on critical accounts: email, banking, cloud storage
- Use authenticator apps over SMS for added security
3. Keep Software Updated
- Install updates for operating systems, browsers, and applications as soon as they’re available
- Many updates patch known security vulnerabilities
4. Secure Your Devices
- Use antivirus software and firewalls
- Enable full-disk encryption on laptops and smartphones
- Set up screen locks and remote wipe in case of loss or theft
5. Be Aware of Phishing
- Don’t click unknown links or attachments in unsolicited emails
- Check sender domains carefully
- When in doubt, verify through another channel
6. Use Trusted Networks
- Avoid performing sensitive transactions on public Wi-Fi
- Use a VPN to encrypt your internet traffic when on unsecured networks
Best Practices for Businesses
Organizations face larger attack surfaces and higher stakes. One breach can lead to financial loss, reputational damage, or legal consequences.
1. Establish a Cybersecurity Policy
- Define acceptable use of devices, data handling rules, and incident reporting procedures
- Align with standards like ISO 27001, NIST, or CIS Controls
2. Provide Regular Security Awareness Training
- Employees are the first line of defense—or vulnerability
- Simulate phishing attacks and conduct periodic refreshers
3. Implement Access Controls
- Enforce least privilege: only grant access necessary for each role
- Use role-based access control (RBAC) for system permissions
4. Monitor and Audit Systems
- Deploy SIEM, IDS/IPS, and real-time alert systems
- Conduct regular audits and vulnerability assessments
5. Have an Incident Response Plan
- Prepare step-by-step procedures for identifying, containing, and recovering from cyber incidents
- Include communication protocols and legal compliance steps
6. Backup Data Frequently
- Follow the 3-2-1 rule: 3 copies of data, 2 different media types, 1 stored offsite or in the cloud
- Test restoration processes regularly
Comparison Table: Individual vs Business Cybersecurity Practices
| Practice Area | Individuals | Businesses |
|---|---|---|
| Password Management | Use password manager, strong passwords | Enforce complexity policies, SSO, credential vaults |
| Software Updates | Enable auto-updates | Patch management systems across endpoints & servers |
| Network Security | Use VPNs, avoid public Wi-Fi | Deploy firewalls, segmentation, network monitoring |
| Threat Awareness | Beware of phishing and scams | Conduct staff training and simulate threats |
| Device Protection | Antivirus, screen locks, encryption | EDR solutions, secure endpoints, mobile device mgmt |
| Data Backup | Cloud or external storage backups | Automated, encrypted, and redundant backups |
| Access Control | Personal device access only | RBAC, MFA, conditional access policies |
| Incident Handling | Manual action or seek tech support | Formal response teams, procedures, legal readiness |
The Role of Cybersecurity in Today’s Digital World
Cybersecurity is no longer a niche concern reserved for IT departments or tech-savvy individuals. It is a foundational requirement for modern society, protecting everything from government systems to daily digital interactions. Without cybersecurity tools, the digital world as we know it would be unstable, unsafe, and unsustainable.
Cybersecurity and Critical Infrastructure
Critical infrastructure includes systems and assets so essential that their incapacity or destruction would have a devastating impact on public health, safety, or economic security. This includes:
- Power grids
- Transportation networks
- Water supply systems
- Financial institutions
- Healthcare systems
These infrastructures are increasingly digital and interconnected—making them prime targets for cyberattacks. In recent years, ransomware has crippled hospitals, disrupted fuel distribution (Colonial Pipeline attack), and even interfered with public transit.
Governments around the world now prioritize cybersecurity as a matter of national security. Initiatives such as the Cybersecurity & Infrastructure Security Agency (CISA) in the U.S. and the European Union Agency for Cybersecurity (ENISA) work to safeguard these vital sectors.
How Cybersecurity Enables Business, Innovation, and Trust
Companies today are driven by digital operations—from customer interactions to supply chain logistics. Cybersecurity plays a central role in:
- Maintaining Trust
A data breach can destroy customer confidence and brand reputation overnight. Effective cybersecurity practices preserve integrity and demonstrate responsibility. - Supporting Innovation
Businesses can confidently explore new technologies like cloud computing, AI, and IoT devices only when they know their digital environments are secure. - Protecting Intellectual Property
For companies in industries like biotech, software, and manufacturing, IP theft through cyber espionage is a major concern. Cybersecurity ensures that R&D investments are protected. - Reducing Downtime and Financial Loss
Cyber incidents can cost millions in recovery, lost revenue, regulatory fines, and legal settlements. Preventative cybersecurity is far more cost-effective than damage control.
Legal and Compliance Considerations
Cybersecurity isn’t just a technical issue—it’s a legal and regulatory one as well. Organizations are now held accountable for how they handle user data and respond to cyber incidents.
Key regulations include:
Regulation Jurisdiction Focus GDPR (General Data Protection Regulation) European Union Requires organizations to protect personal data and report breaches HIPAA (Health Insurance Portability and Accountability Act) United States Sets security standards for handling medical data PCI DSS (Payment Card Industry Data Security Standard) Global Ensures safe handling of credit card transactions CCPA (California Consumer Privacy Act) California, US Gives consumers rights over their personal data Cybersecurity Law of China China Mandates data localization and security assessments for companies operating in China
Non-compliance can result in hefty fines, legal liability, and business restrictions. Thus, cybersecurity must be tightly integrated with an organization’s governance and risk management strategy.
The Future of Cybersecurity: Trends and Emerging Threats

As technology evolves, so do the methods and motivations of cybercriminals. Tomorrow’s threats won’t look like today’s—and defending against them requires staying ahead of the curve. From AI-powered attacks to quantum vulnerabilities, the future of cybersecurity is both promising and perilous.
AI in Cybersecurity—and in Attacks
Artificial Intelligence is revolutionizing both sides of the cybersecurity battlefield.
AI for Defense:
- Threat detection: Machine learning models can spot anomalies in real-time across vast amounts of network traffic.
- Behavioral analytics: AI learns the normal behavior of users/devices to identify insider threats or compromised credentials.
- Automation: AI can automate incident response, reducing reaction time and operational load.
AI for Offense:
- AI-generated phishing: Sophisticated, personalized scam emails using natural language models.
- Malware mutation: AI tools can help attackers generate polymorphic code that evades detection.
- Deepfake and voice clone attacks: Impersonation attacks are becoming harder to spot.
As AI becomes more advanced, cybersecurity professionals will need to leverage it more aggressively while defending against its misuse.
Zero Trust Architecture (ZTA)
The traditional “castle-and-moat” approach to cybersecurity—where users inside the network perimeter are trusted—is obsolete.
Zero Trust flips this model:
- Never trust, always verify
- Every access request is authenticated, authorized, and encrypted regardless of location or device.
Key principles of Zero Trust:
- Micro-segmentation of networks
- Continuous monitoring and verification
- Least privilege access
- Identity and device validation
ZTA is now a standard recommendation from organizations like NIST and is being widely adopted in enterprise and government networks.
Quantum Computing and Encryption Risks
Quantum computers, once fully realized, could break many of today’s cryptographic systems. This threat isn’t imminent, but it’s significant enough that cybersecurity experts are preparing now.
Quantum threat examples:
- Breaking RSA and ECC encryption
- Rendering current public-key infrastructure (PKI) obsolete
The response: Post-Quantum Cryptography (PQC)
Efforts are underway to develop quantum-resistant algorithms. NIST is in the process of standardizing PQC approaches that can withstand quantum attacks.
Rise of Cyber Warfare and Geopolitical Threats
State-sponsored cyberattacks are increasing in frequency, scale, and sophistication.
Notable events:
- SolarWinds attack: Affected U.S. government and Fortune 500 firms
- Stuxnet worm: Disrupted Iranian nuclear infrastructure
- Ukraine power grid attacks: Tied to Russian state-sponsored actors
Nation-states use cyber operations to:
- Steal sensitive data or intellectual property
- Sabotage critical infrastructure
- Spread misinformation or disrupt elections
- Spy on adversaries
Careers in Cybersecurity: Roles, Skills, and Growth Opportunities

As cyber threats grow in complexity and scale, so does the demand for qualified cybersecurity professionals. This field offers high-paying, meaningful, and future-proof career paths across every industry—from government and finance to healthcare and tech startups.
Key Cybersecurity Roles and Responsibilities
Here are some of the most in-demand job titles in cybersecurity, along with what they typically involve:
Role Description Security Analyst Monitors systems for security breaches, analyzes logs, and responds to incidents. Penetration Tester (Ethical Hacker) Simulates attacks to find vulnerabilities before hackers do. Security Engineer Designs and implements secure network solutions and system architectures. Security Architect Develops the overall cybersecurity framework and long-term protection strategy. CISO (Chief Information Security Officer) Oversees the entire cybersecurity strategy of an organization. SOC Analyst (Security Operations Center) Works in a team environment to detect and respond to threats in real time. Threat Intelligence Analyst Tracks and studies threat actors, malware trends, and global cybercrime patterns.
Each role may have a slightly different focus—some technical, some managerial—but all require strong analytical thinking and a commitment to continual learning.
Top Skills and Certifications in Demand
While many cybersecurity roles don’t require a computer science degree, they do demand hands-on skills, certifications, and continuous upskilling.
Essential Technical Skills:
- Network security and protocols (TCP/IP, DNS, VPN, etc.)
- Firewalls, IDS/IPS, and endpoint protection
- Risk assessment and vulnerability management
- SIEM tools (e.g., Splunk, IBM QRadar)
- Incident response and digital forensics
- Secure coding practices (for application security roles)
- Cloud security (AWS, Azure, GCP)
Non-Technical Skills:
- Communication and reporting (especially for governance and compliance)
- Critical thinking and problem-solving
- Project management and leadership
Popular Certifications:
| Certification | Best For | Issuer |
|---|---|---|
| CompTIA Security+ | Entry-level professionals | CompTIA |
| Certified Ethical Hacker (CEH) | Penetration testers and red teamers | EC-Council |
| Certified Information Systems Security Professional (CISSP) | Mid- to senior-level roles | ISC² |
| Certified Cloud Security Professional (CCSP) | Cloud security specialists | ISC² |
| GIAC Security Essentials (GSEC) | Intermediate security practitioners | SANS Institute |
| CISA / CISM | Governance, auditing, and risk managers | ISACA |
Most of these certs can significantly increase your earning potential and job opportunities globally.
Career Outlook and Industry Growth
According to the U.S. Bureau of Labor Statistics (BLS), employment for information security analysts is projected to grow 32% from 2022 to 2032, much faster than the average for all occupations.
Key drivers of growth include:
- Expanding attack surfaces due to cloud, IoT, and remote work
- Growing regulatory pressure on companies to secure data
- High-profile breaches increasing awareness at the board level
- Global cybersecurity talent shortage
In short: Cybersecurity isn’t just a job market—it’s a global talent crisis, and that means massive opportunity for those willing to skill up.
Conclusion
Cybersecurity is no longer a niche concern for IT departments—it’s a critical foundation of trust, safety, and functionality in the digital age. From individuals protecting their personal data to enterprises defending sensitive systems, cybersecurity underpins the operations of our connected world.
We’ve explored how cybersecurity works, the key principles of protection (confidentiality, integrity, availability), the wide range of threats organizations face, and the technologies used to combat them. Whether you’re a user, a business owner, or an aspiring security professional, understanding cybersecurity is not optional—it’s essential.
Looking ahead, the cybersecurity landscape will only grow more complex. But with that complexity comes opportunity: for innovation, for career growth, and for building a safer digital future.
FAQ About Cybersecurity
What is the main goal of cybersecurity?
The main goal of cybersecurity is to protect systems, networks, and data from digital attacks, unauthorized access, damage, or theft. It ensures confidentiality, integrity, and availability of information.
What are the most common types of cyberattacks?
Some of the most frequent types include malware, phishing, ransomware, denial-of-service (DoS/DDoS), man-in-the-middle (MitM) attacks, and insider threats. These attacks aim to exploit vulnerabilities in people, systems, or software.
Can small businesses be targeted by cybercriminals?
Absolutely. In fact, small businesses are often prime targets because they tend to have weaker defenses. Cybersecurity is critical for businesses of all sizes.
How can individuals improve their personal cybersecurity?
Individuals can enhance their security by:
Using strong, unique passwords
Enabling multi-factor authentication (MFA)
Keeping software up to date
Being cautious with suspicious emails and links
Backing up important data
Is a career in cybersecurity worth it?
Yes. Cybersecurity careers are in high demand, well-paid, and offer job security. The field is dynamic, continually evolving, and offers opportunities in both technical and strategic roles across virtually every industry.